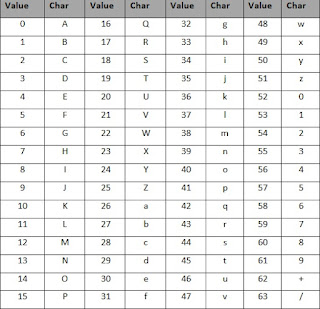
Base64 Algorithm

Encryption And Decryption
# Encryption is the process of converting normal message (plaintext) into meaningless message (Ciphertext).
# Decryption is the process of converting meaningless message (Ciphertext) into its original form (Plaintext).



An encryption algorithm along with a key is used in the encryption and decryption of data. There are several types of data encryptions which form the basis of network security. Encryption schemes are based on block or stream ciphers.
Encryption key.
A sequence of values that are used with a cipher algorithm to encrypt a message. The choice of random (or cryptographically pseudorandom) keys, a secure key exchange mechanism, frequent key refreshments, and good secrecy protection of keys are all essential ingredients for the security of the integrity verification mechanism.

Symmetric encryption algorithm.


Private key.
The secret component of a pair of cryptographic keys used for asymmetric cryptography. In a public key cryptosystem that key of a user's key pair which is known only by that user.
Public key
A public key which encrypts a message. (RFC 2828) The publicly-discloseable component of a pair of cryptographic keys used for asymmetric cryptography. In a public key cryptosystem, that key of a user's key pair which is publicly known.
Public key encryption.
An encryption mechanism where two keys are used. A public key is used to encrypt the message and a secret private key to decrypt the message.
Comments
Post a Comment