Base64 Algorithm
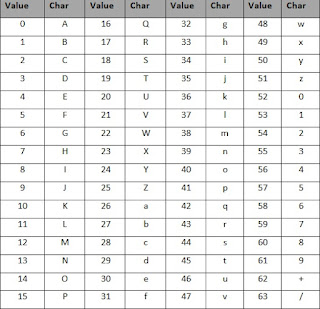
Introduction -----> Base64 encoding is used to c onvert binary data into a text-like format that allows it to be transported in environments that can handle only text safely. -----> Base64 is sometimes also refered to as PEM , which stands for Privacy-enhanced Electronic Mail . There, Base64 was used to create printable text again after binary e-mail data that was generated during the e-mail encryption process. How it works Base64 encoding takes the original binary data and operates on it by dividing it into tokens of three bytes . A byte consists of eight bits, so Base64 takes 24bits in total. These 3 bytes are then converted into four printable characters from the ASCII standard. The first step is to take the three bytes (24...




Comments
Post a Comment